QUESTION 78
You are an experienced ISMS audit team leader providing instruction to an auditor in training. They are unclear in their understanding of risk processes and ask you to provide them with an example of each of the processes detailed below.
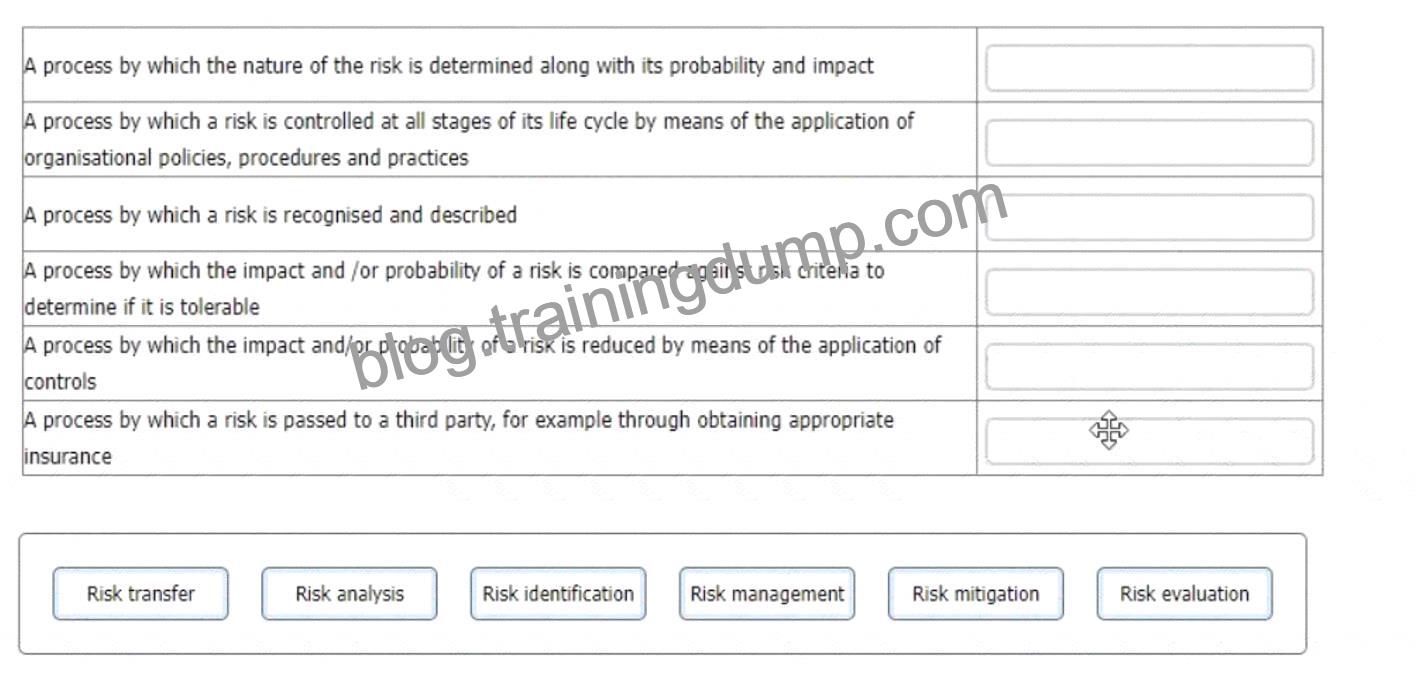
Match each of the descriptions provided to one of the following risk management processes.
To complete the table click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop each option to the appropriate blank section.
Explanation:
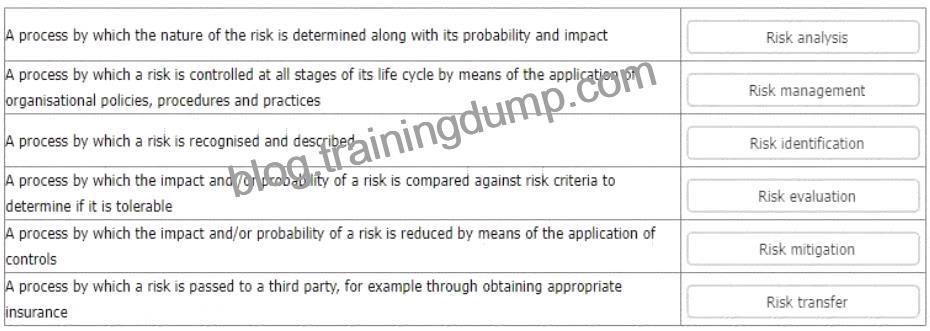
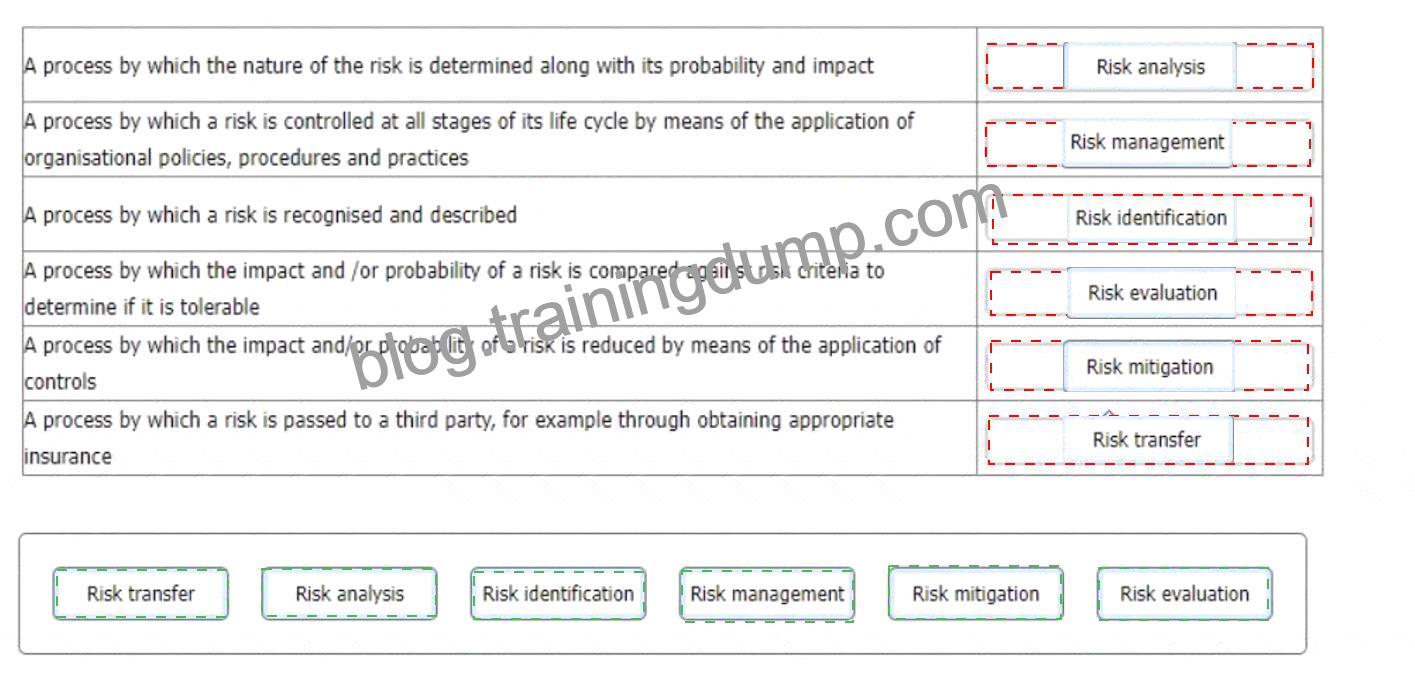
* Risk analysis is the process by which the nature of the risk is determined along with its probability and impact. Risk analysis involves estimating the likelihood and consequences of potential events or situations that could affect the organization’s information security objectives or requirements12. Risk analysis could use qualitative or quantitative methods, or a combination of both12.
* Risk management is the process by which a risk is controlled at all stages of its life cycle by means of the application of organisational policies, procedures and practices. Risk management involves establishing the context, identifying, analyzing, evaluating, treating, monitoring, and reviewing the risks that could affect the organization’s information security performance or compliance12. Risk management aims to ensure that risks are identified and treated in a timely and effective manner, and that opportunities for improvement are exploited12.
* Risk identification is the process by which a risk is recognised and described. Risk identification involves identifying and documenting the sources, causes, events, scenarios, and potential impacts of risks that could affect the organization’s information security objectives or requirements12. Risk identification could use various techniques, such as brainstorming, interviews, checklists, surveys, or historical data12.
* Risk evaluation is the process by which the impact and/or probability of a risk is compared against risk criteria to determine if it is tolerable. Risk evaluation involves comparing the results of risk analysis with predefined criteria that reflect the organization’s risk appetite, tolerance, or acceptance12. Risk evaluation could use various methods, such as ranking, scoring, or matrix12. Risk evaluation helps to prioritize and decide on the appropriate risk treatment options12.
* Risk mitigation is the process by which the impact and/or probability of a risk is reduced by means of the application of controls. Risk mitigation involves selecting and implementing measures that are designed to prevent, reduce, transfer, or accept risks that could affect the organization’s information security objectives or requirements12. Risk mitigation could include various types of controls, such as technical, organizational, legal, or physical12. Risk mitigation should be based on a cost-benefit analysis and a residual risk assessment12.
* Risk transfer is the process by which a risk is passed to a third party, for example through obtaining appropriate insurance. Risk transfer involves sharing or shifting some or all of the responsibility or liability for a risk to another party that has more capacity or capability to manage it12. Risk transfer could include various methods, such as contracts, agreements, partnerships, outsourcing, or insurance12. Risk transfer should not be used as a substitute for effective risk management within the organization12.
References :=
* ISO/IEC 27001:2022 Information technology – Security techniques – Information security management systems – Requirements
* ISO/IEC 27005:2022 Information technology – Security techniques – Information security risk management

Leave a Reply